
Using 350-201 dumps can help you successfully pass the Cisco CBRCOR certification exam on your first attempt.
Because 350-201 dumps have many success advantages:
- Lightweight Learning Tool (PDF+VCE)
- More free usage time (365 days Free Update)
- Covers all Cisco CBRCOR practical exam questions and answers, with explanations of difficult problems
- Have a professional Cisco technical team service
So why not use 350-201 dumps to help you easily and successfully pass the exam? And leads4pass, as the provider of 350-201 dumps, has many years of industry reputation, is the industry leader, and is trustworthy, what else do you have to worry about?
Therefore, it is strongly recommended that you use the 350-201 dumps exam material https://www.leads4pass.com/350-201.html, which is up to date throughout the year, to prepare you for a career leap.
More detailed 350-201 CBRCOR certification information:
Vendor: Cisco
Exam Code: 350-201
Exam Name: Performing CyberOps Using Cisco Security Technologies (CBRCOR)
Certification: CyberOps Professional
Duration: 120 minutes
Languages: English
Price: $400 USD
Number of Questions: 90-110
350-201 dumps: https://www.leads4pass.com/350-201.html (Total Questions: 139 Q&A)
Cisco 350-201 exam questions online practice test:
Tips: Verify the answer at the end of the article
New Question 1:
What is a principle of Infrastructure as Code?
A. System maintenance is delegated to software systems
B. Comprehensive initial designs support robust systems
C. Scripts and manual configurations work together to ensure repeatable routines
D. System downtime is grouped and scheduled across the infrastructure
New Question 2:
Refer to the exhibit. Where are the browser page rendering permissions displayed?
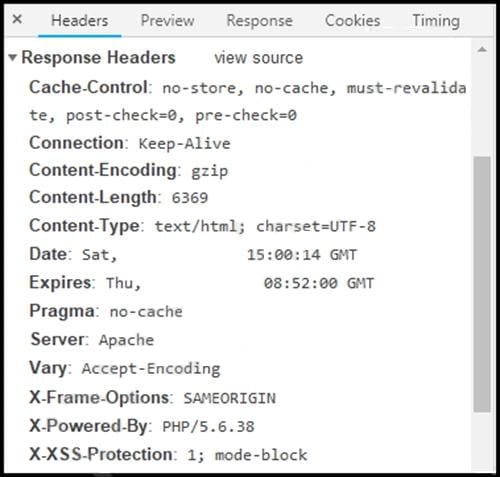
A. X-Frame-Options
B. X-XSS-Protection
C. Content-Type
D. Cache-Control
New Question 3:
Refer to the exhibit. An engineer received multiple reports from employees unable to log into systems with the error: The Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer discovered several unexpected modifications to system settings. Which type of breach is occurring?
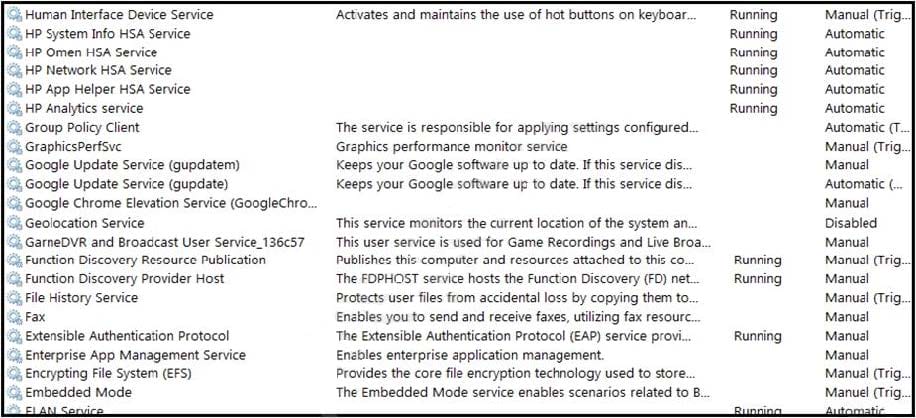
A. malware break
B. data theft
C. elevation of privileges
D. denial-of-service
New Question 4:
How does Wireshark decrypt TLS network traffic?
A. with a key log file using per-session secrets
B. using an RSA public key
C. by observing DH key exchange
D. by defining a user-specified decode-as
Reference: https://wiki.wireshark.org/TLS
New Question 5:
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
A. aligning access control policies
B. exfiltration during data transfer
C. attack using default accounts
D. data exposure from backups
New Question 6:
An organization is using a PKI management server and a SOAR platform to manage the certificate lifecycle. The SOAR platform queries a certificate management tool to check all endpoints for SSL certificates that have either expired or are nearing expiration. Engineers are struggling to manage problematic certificates outside of PKI management since deploying certificates and tracking them requires searching server owners manually.
Which action will improve workflow automation?
A. Implement a new workflow within SOAR to create tickets in the incident response system, assign problematic certificate update requests to server owners, and register change requests.
B. Integrate a PKI solution within SOAR to create certificates within the SOAR engines to track, update, and monitor problematic certificates.
C. Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
D. Integrate a SOAR solution with Active Directory to pull server owner details from the AD and send an automated email for problematic certificates requesting updates.
New Question 7:
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled “Invoice RE: 0004489”. The hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web.
What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A. Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B. Ask the company to execute the payload for real time analysis
C. Investigate further in open source repositories using YARA to find matches
D. Obtain a copy of the file for detonation in a sandbox
New Question 8:
A company recently started accepting credit card payments in their local warehouses and is undergoing a PCI audit. Based on business requirements, the company needs to store sensitive authentication data for 45 days. How must data be stored for compliance?
A. post-authorization by non-issuing entities if there is a documented business justification
B. by entities that issue the payment cards or that perform support issuing services
C. post-authorization by non-issuing entities if the data is encrypted and securely stored
D. by issuers and issuer processors if there is a legitimate reason
New Question 9:
Which bash command will print all lines from the “colors.txt” file containing the non case-sensitive pattern “Yellow”?
A. grep -i “yellow” colors.txt
B. locate “yellow” colors.txt
C. locate -i “Yellow” colors.txt
D. grep “Yellow” colors.txt
New Question 10:
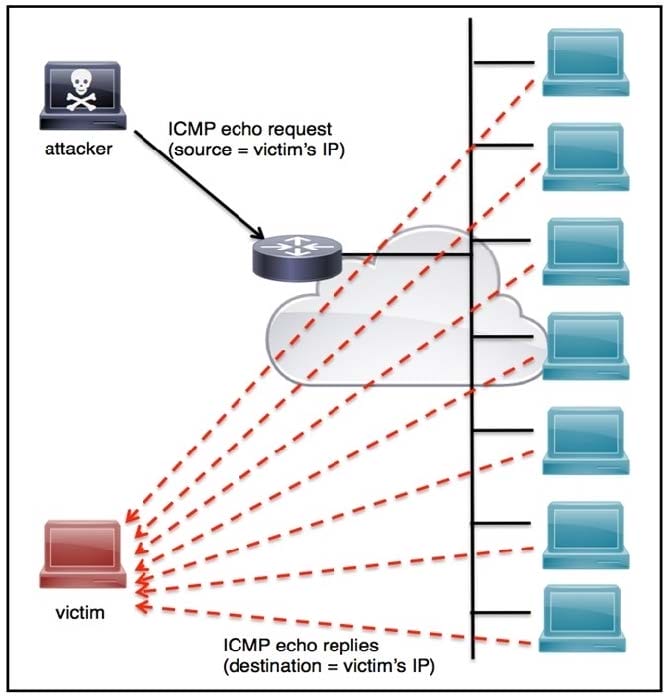
Refer to the exhibit. An engineer must tune the Cisco IOS device to mitigate an attack that is broadcasting a large number of ICMP packets. The attack is sending the victim\’s spoofed source IP to a network using an IP broadcast address that causes devices in the network to respond back to the source IP address.
Which action does the engineer recommend?
A. Use command ip verify reverse-path interface
B. Use global configuration command service tcp-keepalives-out
C. Use subinterface command no ip directed-broadcast
D. Use logging trap 6
Reference: https://www.ccexpert.us/pix-firewall/ip-verify-reversepath-command.html
New Question 11:
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?
A. Block local to remote HTTP/HTTPS requests on the firewall for users who triggered the rule.
B. Inform the user by enabling an automated email response when the rule is triggered.
C. Inform the incident response team by enabling an automated email response when the rule is triggered.
D. Create an automation script for blocking URLs on the firewall when the rule is triggered.
New Question 12:
Refer to the exhibit. A security analyst needs to investigate a security incident involving several suspicious connections with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?

A. packet sniffer
B. malware analysis
C. SIEM
D. firewall manager
New Question 13:
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having the names of the 3 destination countries and the user\’s working hours, what must the analyst do next to detect an abnormal behavior?
A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
B. Create a rule triggered by 1 successful VPN connection from any nondestination country
C. Create a rule triggered by multiple successful VPN connections from the destination countries
D. Analyze the logs from all countries related to this user during the traveling period
New Question 14:
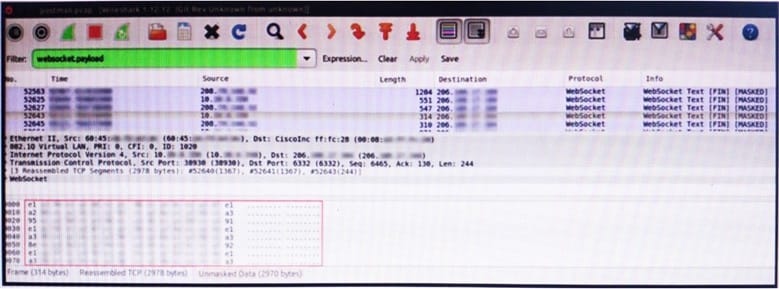
Refer to the exhibit. An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious network activity. The origin header for the direct IP connections in the packets was initiated by a google chrome extension on a WebSocket protocol. The engineer checked message payloads to determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
A. The extension is not performing as intended because of restrictions since ports 80 and 443 should be accessible
B. The traffic is legitimate as the google chrome extension is reaching out to check for updates and fetches this information
C. There is a possible data leak because payloads should be encoded as UTF-8 text
D. There is a malware that is communicating via encrypted channels to the command and control server
New Question 15:
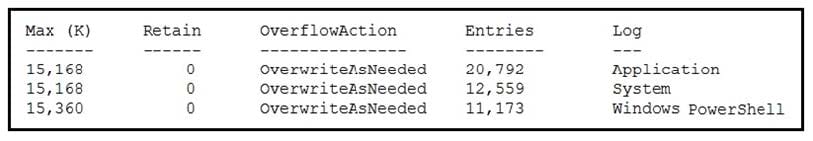
Refer to the exhibit. An employee is a victim of a social engineering phone call and installs remote access software to allow an “MS Support” technician to check his machine for malware. The employee becomes suspicious after the remote technician requests payment in the form of gift cards. The employee has copies of multiple, unencrypted database files, over 400 MB each, on his system and is worried that the scammer copied the files off but has no proof of it. The remote technician was connected sometime between 2:00 pm and 3:00 pm over https.
What should be determined regarding data loss between the employee\’s laptop and the remote technician\’s system?
A. No database files were disclosed
B. The database files were disclosed
C. The database files integrity was violated
D. The database files were intentionally corrupted, and encryption is possible
…
Verify answer:
| Numbers: | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers: | B | C | C | A | B | C | D | C | A | A | A | A | D | C | C |
Cisco Certified CyberOps Professional certification includes: The core exam and Concentration exams, Cisco CBRCOR certification exam belongs to the Core exam (350-201 CBRCOR) and is unique.
Select leads4pass 350-201 dumps https://www.leads4pass.com/350-201.html, Helping you 100% pass the Cisco 350-201 CBRCOR certification exam. All Cisco Certified CyberOps Professional certification programs are available in leads4pass and can ensure that you pass the exam with a high score.