Continue to share the newly updated 350-701 Dumps. Contains 542 new exam questions and answers, not only many more questions than the previous 392 exams but also fully updated all exam questions and answers.
leads4pass 350-701 Dumps provides 350-701 PDF files and 350-701 VCE mock exam engine to study the latest 542 exam questions, so candidates only need to visit: https://www.leads4pass.com/350-701.html were able to Download the desired brain dump content to help you win easily.
| Number of exam questions | Exam name | From | Release time | Previous issue |
| 13 | Implementing and Operating Cisco Security Core Technologies (SCOR) | leads4pass | Oct 12, 2022 | 350-701 dumps questions (Q1-Q13) |
Continue to study the latest 13 free 350-701 exam questions:
NEW QUESTION 14:
On which part of the IT environment does DevSecOps focus?
A. application development
B. wireless network
C. data center
D. perimeter network
Correct Answer: A
NEW QUESTION 15:
An organization wants to implement a cloud-delivered and SaaS-based solution to provide visibility and threat detection across the AWS network. The solution must be deployed without software agents and rely on AWS VPC flow logs instead.
Which solution meets these requirements?
A. NetFlow collectors
B. Cisco Cloudlock
C. Cisco Stealthwatch Cloud
D. Cisco Umbrella
Correct Answer: C
Reference: https://www.cisco.com/c/en/us/products/security/stealthwatch-cloud/index.html
NEW QUESTION 16:
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The company needs to be able to protect sensitive data throughout the full environment.
Which tool should be used to accomplish this goal?
A. Security Manager
B. Cloudlock
C. Web Security Appliance
D. Cisco ISE
Correct Answer: B
Cisco Cloudlock is a cloud-native cloud access security broker (CASB) that helps you move to the cloud safely. It protects your cloud users, data, and apps.
Cisco Cloudlock provides visibility and compliance checks, protects data against misuse and exfiltration, and provides threat protections against malware like ransomware.
NEW QUESTION 17:
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access?
A. Cisco Container Platform
B. Cisco Content Platform
C. Cisco Cloud Platform
D. Cisco Container Controller
Correct Answer: A
NEW QUESTION 18:
Why should organizations migrate to an MFA strategy for authentication?
A. Single methods of authentication can be compromised more easily than MFA.
B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily.
C. MFA methods of authentication are never compromised.
D. MFA does not require any piece of evidence for an authentication mechanism.
Correct Answer: A
NEW QUESTION 19:
A company discovered an attack propagating through its network via a file. A custom file policy was created in order to track this in the future and ensure no other endpoints execute the infected file.
In addition, it was discovered during testing that the scans are not detecting the file as an indicator of compromise.
What must be done in order to ensure that the created is functioning as it should?
A. Create an IP block list for the website from which the file was downloaded
B. Block the application that the file was used to open
C. Upload the hash for the file into the policy
D. Send the file to Cisco Threat Grid for dynamic analysis
Correct Answer: C
NEW QUESTION 20:
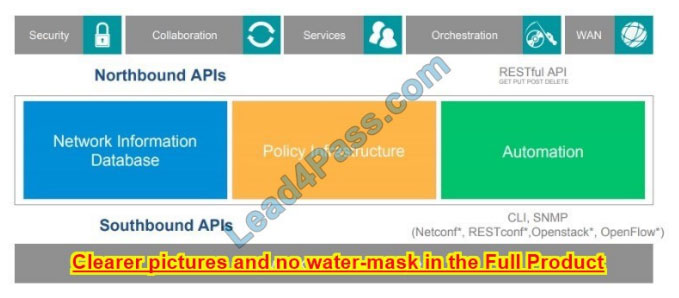
What are the two functionalities of northbound and southbound APIs within Cisco SDN architecture? (Choose two.)
A. Southbound APIs utilize CLI, SNMP, and RESTCONF.
B. Southbound interfaces utilize device configurations such as VLANs and IP addresses.
C. Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE.
D. Southbound APIs are used to define how SDN controllers integrate with applications.
E. Northbound interfaces utilize OpenFlow and OpFlex to integrate with network devices.
Correct Answer: AC
NEW QUESTION 21:
A malicious user gained network access by spoofing printer connections that were authorized using MAB on four different switch ports at the same time.
What two catalyst switch security features will prevent further violations? (Choose two)
A. DHCP Snooping
B. 802.1AE MacSec
C. Port security
D. IP Device track
E. Dynamic ARP inspection
F. Private VLANs
Correct Answer: AE
NEW QUESTION 22:

Refer to the exhibit. All servers are in the same VLAN/Subnet DNS Server-1 and DNS Server-2 must communicate with each other and all servers must communicate with the default gateway multilayer switch.
Which types of private VLAN ports should be configured to prevent communication between DNS servers and the file server?
A. Configure GigabitEthemet0/1 as a community port, GigabitEthernet0/2 as a promiscuous port GigabitEthernet0/3, and GigabitEthernet0/4 as isolated ports
B. Configure GigabitEthernet0/1 as a promiscuous port, GigabitEthernet0/2 as an isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as community ports
C. Configure GigabitEthernet0/1 as a promiscuous port, GigabitEthernet0/2 as a community port, and GigabitEthernet0/3 and Gigabit Ethernet0/4 as isolated ports
D. Configure GigabitEthernet0/1 as a community port GigabitEthernet0/2 as an isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as promiscuous ports
Correct Answer: B
NEW QUESTION 23:
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
A. LDAP injection
B. man-in-the-middle
C. cross-site scripting
D. insecure API
Correct Answer: B
NEW QUESTION 24:
What is the benefit of performing device compliance?
A. Verification of the latest OS patches
B. Device classification and authorization
C. Providing multi-factor authentication
D. Providing attribute-driven policies
Correct Answer: A
NEW QUESTION 25:
While using Cisco Firepower\’s Security Intelligence policies, which two criteria is blocking based upon? (Choose two.)
A. port numbers
B. URLS
C. IP addresses
D. protocol IDs
E. MAC addresses
Correct Answer: BC
NEW QUESTION 26:
Where are individual sites specified to be blacklisted in Cisco Umbrella?
A. application settings
B. content categories
C. security settings
D. destination lists
Correct Answer: D
Reference: https://docs.umbrella.com/deployment-umbrella/docs/working-with-destination-lists
…
Candidates are welcome to download the latest and updated Cisco 350-701 exam materials: https://www.leads4pass.com/350-701.html (PDF + VCE 542 Q&A). Practice the full 350-701 exam questions and answer guarantee provided by leads4pass You pass the exam 100%.
BTW, download the latest free 350-701 exam questions and answers from Google Drive:https://drive.google.com/file/d/1nrGX0OHNPH6_sX2MlYWI8i4jCVVOUV7g/view?usp=sharing