
The latest update of Cisco 350-401 exam questions and answers comes from leads4pass Cisco experts verify that they are true and valid, and the 580 Q&A is fully updated. leads4pass 350-401 https://www.leads4pass.com/350-401.html.
And Cisco 350-401 exam practice questions test verification! Improve strength and skills! This site shares the complete series of cisco free dumps, please bookmark and share to help more people pass the exam.
Free Cisco 350-401 exam PDF download online
Google Drive: https://drive.google.com/file/d/15h0DjxRwaAnbZHDRbrXPvHru6FM9_A50/view?usp=sharing
Take the Cisco 350-401 online exam test
The answer is announced at the end of the article
QUESTION 1
Which unit is used to express the signal-to-noise ratio?
A. mW
B. db
C. amp
D. dbm
QUESTION 2
Which two mechanisms are available to secure NTP? (Choose two.)
A. IP prefix list-based
B. IPsec
C. TACACS-based authentication
D. IP access list-based
E. Encrypted authentication
The time kept on a machine is a critical resource and it is strongly recommend that you use the security features of NTP to avoid the accidental or malicious setting of incorrect time. The two security features available are an access listbased restriction scheme and an encrypted authentication mechanism.
QUESTION 3
Which outbound access list, applied to the WAN interface of a router, permits all traffic except for http traffic sourced from the workstation with IP address 10.10.10.1?
A. ip access-list extended 10 deny tcp host 10.10.10.1 any eq 80 permit ip any any
B. ip access-list extended 200 deny tcp host 10.10.10.1 eq 80 any permit ip any any
C. ip access-list extended NO_HTTP deny tcp host 10.10.10 1 any eq 80
D. ip access-list extended 100 deny tcp host 10.10.10.1 any eq 80 permit ip any any
QUESTION 4
What is the structure of a JSON web token?
A. three parts separated by dots: header payload, and signature
B. header and payload
C. three parts separated by dots: version header and signature
D. payload and signature
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely
transmitting information between parties as a JSON object. This information can be verified and trusted because it is
digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or
ECDSA. JSON Web Tokens are composed of three parts, separated by a dot (.): Header, Payload, Signature.
Therefore, a JWT typically looks like the following: xxxxx.yyyyy.zzzzz The header typically consists of two parts: the type
of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA. The second part of the token is the payload, which contains the claims. Claims are statements about an entity (typically, the user) and additional data. To create the signature part you have to take the encoded header, the encoded payload, a secret, the
algorithm specified in the header, and sign that.
Reference: https://jwt.io/introduction/
QUESTION 5
What is the function of the fabric control plane node In a Cisco SD-Access deployment?
A. It is responsible for policy application and network segmentation in the fabric.
B. It performs traffic encapsulation and security profiles enforcement in the fabric.
C. It holds a comprehensive database that tracks endpoints and networks in the fabric.
D. It provides Integration with legacy nonfabric-enabled environments.
Fabric control plane node (C): One or more network elements that implement the LISP Map-Server (MS) and MapResolver (MR) functionality. The control plane node`s host tracking database keep track of all endpoints in a fabric site and associates the endpoints to fabric nodes in what is known as an EID-to-RLOC binding in LISP.
QUESTION 6
What are two reasons why broadcast radiation is caused in the virtual machine environment? (Choose two.)
A. vSwitch must interrupt the server CPU to process the broadcast packet.
B. The Layer 2 domain can be large in virtual machine environments.
C. Virtual machines communicate primarily through broadcast mode.
D. Communication between vSwitch and network switch is broadcast based.
E. Communication between vSwitch and network switch is multicast based.
Broadcast radiation is the accumulation of broadcast and multicast traffic on a computer network. Extreme amounts of broadcast traffic constitute a broadcast storm. The amount of broadcast traffic you should see within a broadcast domain is directly proportional to the size of the broadcast domain. Therefore if the layer 2 domain in virtual machine environment is too large, broadcast radiation may occur -> VLANs should be used to reduce broadcast radiation. Also if virtual machines communicate via broadcast too much, broadcast radiation may occur. Another reason for broadcast radiation is using a trunk (to extend VLANs) from the network switch to the physical server.
Note about the structure of virtualization in a hypervisor:
Hypervisors provide virtual switch (vSwitch) that Virtual Machines (VMs) use to communicate with other VMs on the same host. The vSwitch may also be connected to the host\\’s physical NIC to allow VMs to get layer 2 access to the outside world. Each VM is provided with a virtual NIC (vNIC) that is connected to the virtual switch. Multiple vNICs can connect to a single vSwitch, allowing VMs on a physical host to communicate with one another at layer 2 without having to go out to a physical switch.
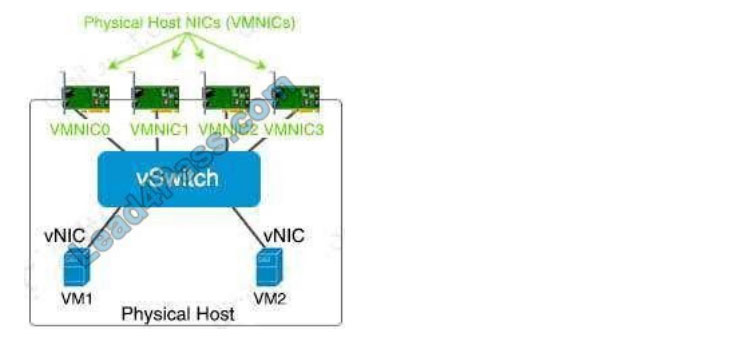
Although vSwitch does not run Spanning-tree protocol but vSwitch implements other loop prevention mechanisms. For example, a frame that enters from one VMNIC is not going to go out of the physical host from a different VMNIC card.
QUESTION 7
Refer to the exhibit. What does the output confirm about the switch\\’s spanning tree configuration?
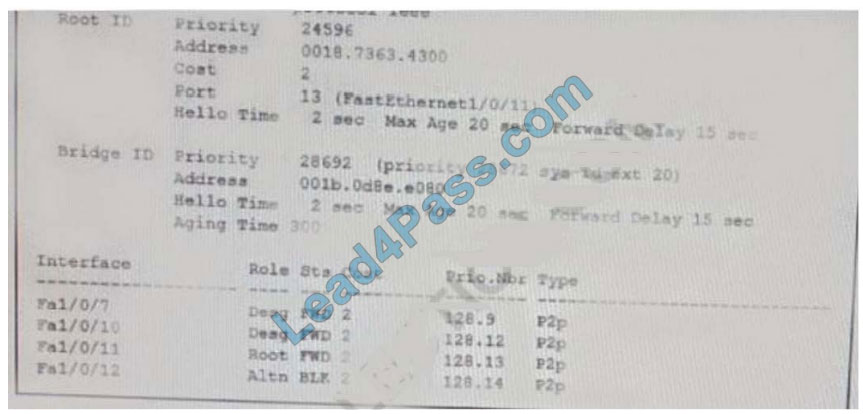
A. The spanning-tree mode stp ieee command was entered on this switch
B. The spanning-tree operation mode for this switch is PVST.
C. The spanning-tree operation mode for this switch is PVST+.
D. The spanning-tree operation mode for this switch is IEEE
QUESTION 8
What is one fact about Cisco SD-Access wireless network deployments?
A. The access point is part of the fabric underlay
B. The WLC is part of the fabric underlay
C. The access point is part the fabric overlay
D. The wireless client is part of the fabric overlay
Access Points
+
AP is directly connected to FE (or to an extended node switch)
+
AP is part of Fabric overlay
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2018/pdf/BRKEWN-2020.pdf
QUESTION 9
Which two pieces of information are necessary to compute SNR? (Choose two.)
A. EIRP
B. noise floor
C. antenna gain
D. RSSI
E. transmit power
signal-to-noise ratio (SNR) A measure of received signal quality, calculated as the difference between the signal\\’s RSSI and the noise floor. A higher SNR is preferred.
QUESTION 10
DRAG DROP
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:
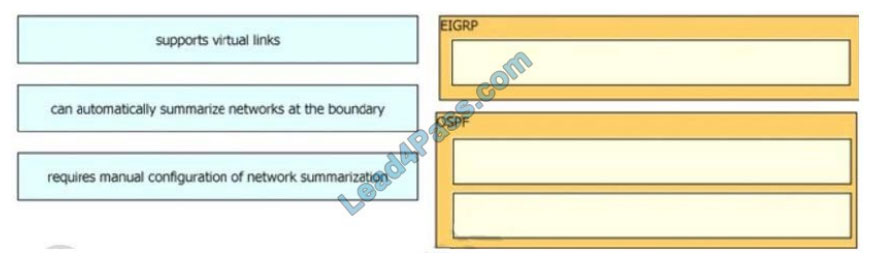
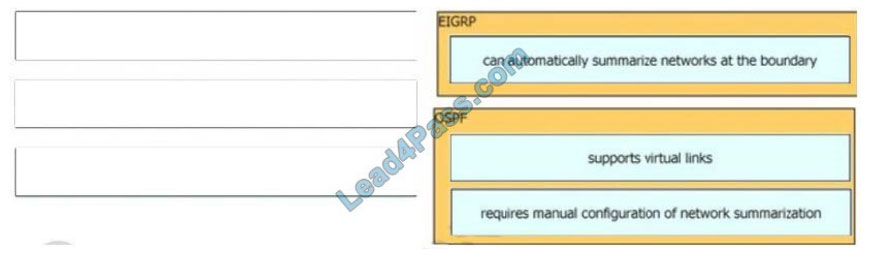
Correct Answer:
QUESTION 11
An engineer uses the Design workflow to create a new network infrastructure in Cisco DNA Center. How is the physical network device hierarchy structured?
A. by location
B. by role
C. by organization
D. by hostname naming convention
QUESTION 12
Which entity is a Type 1 hypervisor?
A. Oracle VM VirtualBox
B. VMware server
C. Citrix XenServer
D. Microsoft Virtual PC
QUESTION 13
What is the recommended MTU size for a Cisco SD-Access Fabric?
A. 1500
B. 9100
C. 4464
D. 17914
Publish the answer
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| B | DE | D | A | C | AB | C | C | BD | IMAGE | A | C | B |
Free Cisco 350-401 exam PDF download online
Google Drive: https://drive.google.com/file/d/15h0DjxRwaAnbZHDRbrXPvHru6FM9_A50/view?usp=sharing
This is a very useful article. Although there are not many descriptions, they can definitely help you successfully pass the Cisco 350-401 exam. Click here https://www.leads4pass.com/350-401.html. Get the complete Cisco 350-401 exam questions to help you succeed on the first exam.