leads4pass -latest updated Cisco CCNP 350-401 test questions and answers.
All test questions have been corrected and updated to ensure that they are true and valid. You can also practice the actual exam questions in the Cisco 350-401 section online.
If you want to get the complete Cisco 350-401 exam questions and answers, you can get them in leads4pass.
leads4pass 350-401 exam dumps include VCE dumps and PDF dumps. Cisco 350-401 exam
“Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)” https://www.leads4pass.com/350-401.html (total questions: 544 questions and answers)
[Free Part] Cisco 350-401 pdf free from leads4pass
Free share Cisco 350-401 exam PDF from Google Drive provided by leads4pass
https://drive.google.com/file/d/1vQQP_btqsNuWkgsO4GQD6a6TukqwujoU/
[Free Part] Cisco 350-401 online exam practice questions from leads4pass
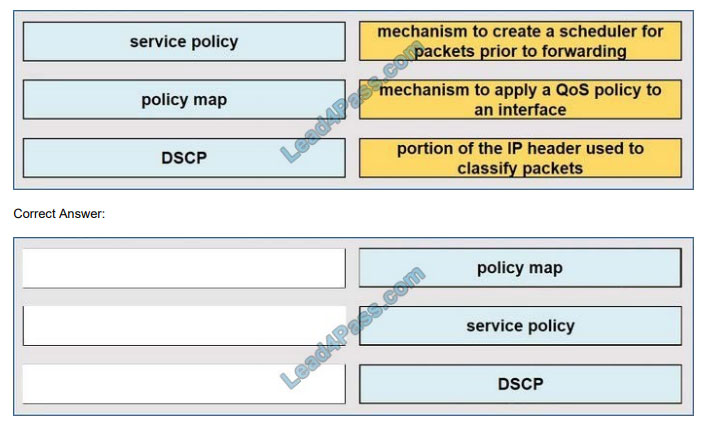
QUESTION 1
DRAG DROP Drag and drop the Qos mechanisms from the left to the correct descriptions on the right
Select and Place:
QUESTION 2
In a traditional 3 tier topology, an engineer must explicitly configure a switch as the root bridge and exclude it from any
further election process for the spanning-tree domain. Which action accomplishes this task?
A. Configure the spanning-tree priority to 32768
B. Configure root guard and portfast on all access switch ports.
C. Configure BPDU guard in all switch-to-switch connections.
D. Configure the spanning-tree priority equal to 0.
Correct Answer: B
Root guard does not allow the port to become a STP root port, so the port is always STP-designated. If a better BPDU
arrives on this port, root guard does not take the BPDU into account and elect a new STP root. Instead, root guard puts
the port into the root-inconsistent STP state which is equal to a listening state. No traffic is forwarded across this port.
Reference: http://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10588-74.html
QUESTION 3
What function does vxlan perform in an SD-Access deployment?
A. policy plane forwarding
B. control plane forwarding
C. data plane forwarding
D. systems management and orchestration
Correct Answer: C
QUESTION 4
Which LISP infrastructure device provides connectivity between non-sites and LISP sites by receiving non-LISP traffic
with a LISP site destination?
A. PETR
B. PITR
C. map resolver
D. map server
Correct Answer: B
Proxy ingress tunnel router (PITR): answer \\’PETR\\’ PITR is an infrastructure LISP network entity that receives packets
from non-LISP sites and encapsulates the packets to LISP sites or natively forwards them to non-LISP sites.
Reference: https://www.ciscopress.com/articles/article.asp?p=2992605 https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Data_Center/DCI/5-0/LISPmobility/DCI_LISP_Host_Mobility/LISPmobile_2.html
QUESTION 5
An engineer must protect their company against ransom ware attacks. Which solution allows the engineer to block the
execution stage and prevent file encryption?
A. Use Cisco AMP deployment with the Malicious Activity Protection engineer enabled.
B. Use Cisco AMP deployment with the Exploit Prevention engine enabled.
C. Use Cisco Firepower and block traffic to TOR networks.
D. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation.
Correct Answer: A
Ransomware are malicious software that locks up critical resources of the users. Ransomware uses well-established
public/private key cryptography which leaves the only way of recovering the files being the payment of the ransom, or
restoring files from backups. Cisco Advanced Malware Protection (AMP) for Endpoints Malicious Activity Protection
(MAP) engine defends your endpoints by monitoring the system and identifying processes that exhibit malicious
activities when they execute and stops them from running. Because the MAP engine detects threats by observing the
behavior of the process at run time, it can generically determine if a system is under attack by a new variant of
ransomware or malware that may have eluded other security products and detection technology, such as legacy
signature-based malware detection. The first release of the MAP engine targets identification, blocking, and quarantine
of ransomware attacks on the endpoint.
https://www.cisco.com/c/dam/en/us/products/collateral/security/amp-for-endpoints/white-paper-c11-740980.pdf
QUESTION 6
A customer has recently implemented a new wireless infrastructure using WLC-5520S at a site directly next to a large
commercial airport Users report that they intermittently lose Wi-Fi connectivity, and troubleshooting reveals it is due to
frequent channel changes Which two actions fix this issue? (Choose two)
A. Remove UNII-2 and Extended UNII-2 channels from the 5 Ghz channel list
B. Restore the OCA default settings because this automatically avoids channel interference
C. Disable DFS channels to prevent interference writ) Doppler radar
D. Enable DFS channels because they are immune to radar interference
E. Configure channels on the UNII-2 and the Extended UNII-2 sub-bands of the 5 Ghz band only
Correct Answer: AC
QUESTION 7
How does Cisco Trustsec enable more access controls for dynamic networking environments and data centers?
A. uses flexible NetFlow
B. assigns a VLAN to the endpoint
C. classifies traffic based an the contextual identity of the endpoint rather than its IP address
D. classifies traffic based on advanced application recognition
Correct Answer: C
QUESTION 8
Witch two actions provide controlled Layer 2 network connectivity between virtual machines running on the same
hypervisor? (Choose two.)
A. Use a single trunk link to an external Layer2 switch.
B. Use a virtual switch provided by the hypervisor.
C. Use a virtual switch running as a separate virtual machine.
D. Use a single routed link to an external router on stick.
E. Use VXLAN fabric after installing VXLAN tunneling drivers on the virtual machines.
Correct Answer: AB
QUESTION 9
Refer to the exhibit.

Only administrators from the subnet 10.10.10.0/24 are permitted to have access to the router. A secure protocol must
be used for the remote access and management of the router instead of clear- text protocols. Which configuration
achieves this goal?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: B
QUESTION 10
A response code of 404 is received while using the REST API on Cisco DNA Center to POST to this URI:
/dna/intent/api/v1/template-programmer/project
What does the code mean?
A. The POST/PUT request was fulfilled and a new resource was created. Information about the resource is in the
response body.
B. The request was accepted for processing, but the processing was not completed.
C. The client made a request for a resource that does not exist.
D. The server has not implemented the functionality that is needed to fulfill the request.
Correct Answer: C
Reference: https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-infrastructure-controlle
r-enterprise-module/1-2-x/config-guide/b_apic-em_config_guide_v_1-2-x/b_apicem_config_guide_v_1-2x_chapter_01001.html
QUESTION 11
What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
A. real-time threat management to stop DDoS attacks to the core and access networks
B. real-time awareness of users, devices and traffic on the network
C. malware control
D. dynamic threat control for web traffic
Correct Answer: B
Cisco Stealthwatch is a comprehensive, network telemetry-based, security monitoring and analytics solution that
streamlines incident response through behavioral analysis; detecting denial of service attacks, anomalous behaviour,
malicious
activity and insider threats. Based on a scalable enterprise architecture, Stealthwatch provides near real-time situational
awareness of all users and devices on the network.
Reference: https://www.endace.com/cisco-stealthwatch-solution-brief.pdf
Note: Although answer A seems to be correct but in fact, Stealthwatch does not provide real-time protection for DDoS
attack. It just helps detect DDoS attack only.
Stealthwatch aggregates observed network activity and performs behavioral and policy driven analytics against what it
sees in order to surface problematic activities. While we don\\’t position our self as a DDOS solution, we’re going to
leverage our analytical capabilities to identify a DDoS attack against an internal host using the WebUI.
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2016/pdf/LTRSEC-8421-LG.pdf
QUESTION 12
What would be the preferred way to implement a loopless switch network where there are 1500 defined VLANs and it is
necessary to load the shared traffic through two main aggregation points based on the VLAN identifier?
A. 802.1D
B. 802.1s
C. 802.1W
D. 802.1AE
Correct Answer: B
QUESTION 13
Refer to the exhibit. Which configuration must be applied to R1 to enable R1 to reach the server at 172.16.0.1?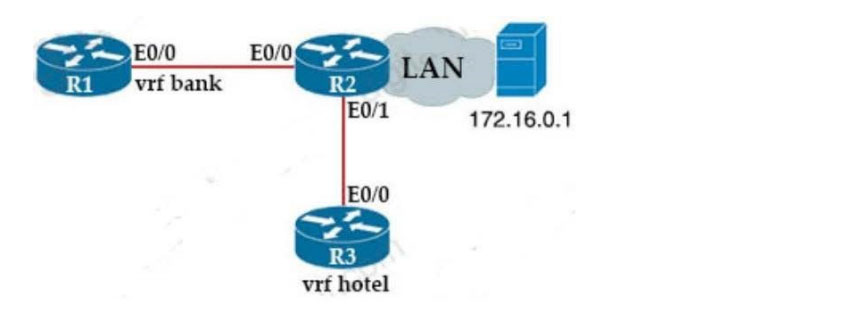
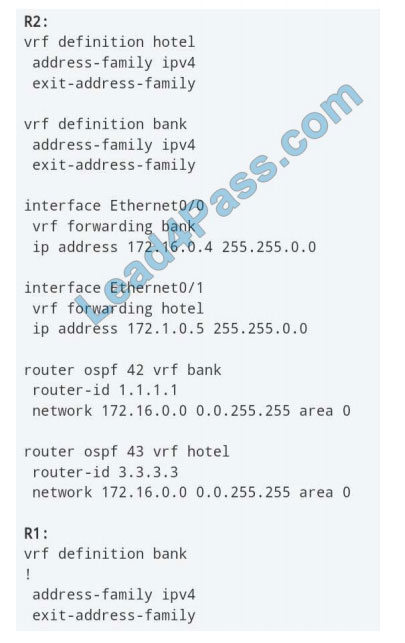
A. interface Ethernet0/0 ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf hotel
network 172.16.0.0 255.255.0.0
B. interface Ethernet0/0 vrf forwarding hotel ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf Hotel
network 172.16.0.0 0.0.255.255 area 0
C. interface Ethernet0/0 vrf forwarding bank ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf bank
network 172.16.0.0 0.0.255.255 area 0
D. interface Ethernet0/0 ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf bank
network 172.16.0.0 0.0.255.255
Correct Answer: C
Cisco CCNP 350-401 exam questions and answers have been updated and corrected! Guaranteed to be true and effective! leads4pass has the most complete exam policy!
If the exam is unsuccessful, a full refund will be issued! To pass the Cisco 350-401 exam, please click: https://www.leads4pass.com/350-401.html (PDF + VCE) to get the key to successfully passing the exam!
wish you success!
[Free Part] Get free Cisco 350-401 exam PDF online: https://drive.google.com/file/d/1vQQP_btqsNuWkgsO4GQD6a6TukqwujoU/