
Successfully passing the Cisco 350-401 exam to obtain certification makes it easy for you to become a top talent.
“Cisco CCNP 350-401 contains many latest technologies:
Dual stack (IPv4 and IPv6) architecture,Virtualization,Infrastructure,Network assurance,Security,Automation”
It is not a simple matter to obtain Cisco CCNP 350-401 certification: first, you need to pay the exam fee of 400 dollars,
secondly, you need to learn a lot of professional knowledge for the exam, and finally, you need to take the exam.
This kind of process does not guarantee that you will pass the exam. Every year, many people cannot pass the exam smoothly!
I’m not trying to discourage everyone’s confidence, I just say that the Cisco CCNP 350-401 exam is not easy!
So I share 13 valid Cisco 350-401 exam questions for free to help you improve your skills and exam experience!
All the exam questions I shared are the latest updates! All 350-401 exam dumps come from leads4pass.com!
leads4pass will help you save a lot of money and help you pass the exam successfully for the first time! And we have the best exam credibility! You are not the first to need us!
Table Of Content:
- Download Cisco 350-401 exam pdf online
- Cisco 350-401 exam video from Youtube
- The latest updated Cisco 350-401 exam practice questions
- Cisco 350-401 Exam Certification Coupon Code 2021
[Cisco 350-401 exam pdf online for free] Share the Cisco 350-401 Dumps PDF for free From leads4pass 350-401 Dumps part of the distraction collected on Google Drive shared by leads4pass
https://drive.google.com/file/d/1aqRKfJ-HNAIYoPpKINhJZh-wSL0b07KL/
[Latest leads4pass 350-401 Youtube] Share the latest Cisco 350-401 exam practice questions and answers for free from Led4Pass Dumps viewed online by Youtube Videos
Cisco CCNP 350-401 exam question and answer online practice exam
QUESTION 1
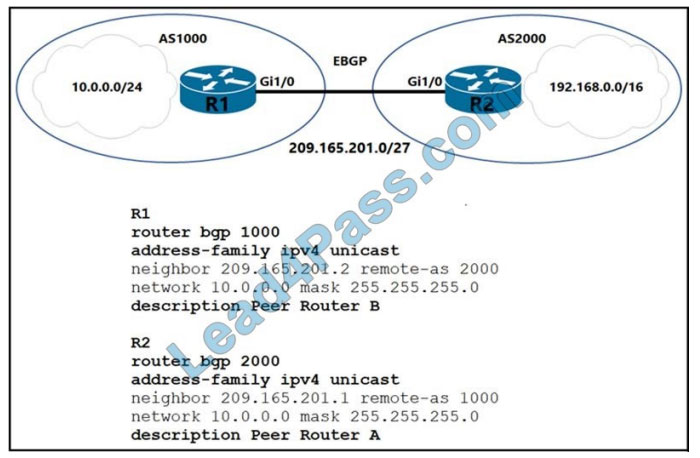
Refer to the exhibit. Which two commands are needed to allow for full reachability between AS 1000 and AS 2000?
(Choose two.)
A. R2#no network 10.0.0.0 255.255.255.0
B. R2#network 209.165.201.0 mask 255.255.192.0
C. R2#network 192.168.0.0 mask 255.255.0.0
D. R1#no network 10.0.0.0 255.255.255.0
E. R1#network 192.168.0.0 mask 255.255.0.0
Correct Answer: AC
QUESTION 2
In a wireless Cisco SD-Access deployment, which roaming method is used when a user moves from one access point
to another on a different access switch using a single WLC?
A. Layer 3
B. inter-xTR
C. auto anchor
D. fast roam
Correct Answer: D
https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2018/pdf/BRKEWN-2020.pdf
QUESTION 3
In OSPF, which LAS type is responsible for pointing to the ASBR router?
A. type 1
B. type 2
C. type 3
D. type 4
Correct Answer: D
QUESTION 4
When a wireless client roams between two different wireless controllers, a network connectivity outage is experienced
for a period of time. Which configuration issue would cause this problem?
A. Not all of the controllers in the mobility group are using the same mobility group name.
B. Not all of the controllers within the mobility group are using the same virtual interface IP address.
C. All of the controllers within the mobility group are using the same virtual interface IP address.
D. All of the controllers in the mobility group are using the same mobility group name.
Correct Answer: B
A prerequisite for configuring Mobility Groups is “All controllers must be configured with the same virtual interface IP
address”. If all the controllers within a mobility group are not using the same virtual interface, inter-controller roaming
may appear to work, but the handoff does not complete, and the client loses connectivity for a period of time. -> Answer
B is correct.
Reference: https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-5/config-guide/b_cg85/mobility_groups.html http
s://www.cisco.com/c/en/us/support/docs/wireless/4400-series-wireless-lan-controllers/107188-mobility-groups-faq.html
QUESTION 5
Which tool is used in Cisco DNA Center to build generic configurations that are able to be applied on a device with similar
network settings?
A. Command Runner
B. Template Editor
C. Application Policies
D. Authentication Template
Correct Answer: B
Cisco DNA Center provides an interactive editor called Template Editor to author CLI templates. Template Editor is a
centralized CLI management tool to help design a set of device configurations that you need to build devices in a
branch. When you have a site, office, or branch that uses a similar set of devices and configurations, you can use
Template Editor to build generic configurations and apply the configurations to one or more devices in the branch.
Reference: https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/dna-center/1-3/user_guide/b_cisco_dna_center_ug_1_3/b_cisco_dna_center_ug_1_3_chapter_0111.html
QUESTION 6
Which two GRE features are configured to prevent fragmentation? (Choose two.)
A. TCP MSS
B. PMTUD
C. DF bit Clear
D. MTU ignore
E. IP MTU
F. TCP window size
Correct Answer: AB
The IP protocol was designed for use on a wide variety of transmission links. Although the maximum length of an IP
datagram is 65535, most transmission links enforce a smaller maximum packet length limit, called an MTU. The value of
the
MTU depends on the type of transmission link. The design of IP accommodates MTU differences since it allows
routers to fragment IP datagrams as necessary. The receiving station is responsible for the reassembly of the fragments
back
into the original full-size IP datagram. Fragmentation and Path Maximum Transmission Unit Discovery (PMTUD) is a
standardized technique to determine the maximum transmission unit (MTU) size on the network path between two
hosts,
usually with the goal of avoiding IP fragmentation. PMTUD was originally intended for routers in IPv4. However, all
modern operating systems use it on endpoints. The TCP Maximum Segment Size (TCP MSS) defines the maximum
amount
of data that a host is willing to accept in a single TCP/IP datagram. This TCP/IP datagram might be fragmented at the IP
layer. The MSS value is sent as a TCP header option only in TCP SYN segments. Each side of a TCP connection
reports its MSS value to the other side. Contrary to popular belief, the MSS value is not negotiated between hosts. The
sending host is required to limit the size of data in a single TCP segment to a value less than or equal to the MSS
reported
by the receiving host. TCP MSS takes care of fragmentation at the two endpoints of a TCP connection, but it does not
handle the case where there is a smaller MTU link in the middle between these two endpoints. PMTUD was developed
in
order to avoid fragmentation in the path between the endpoints. It is used to dynamically determine the lowest MTU
along the path from a packet\\’s source to its destination.
Reference:
http://www.cisco.com/c/en/us/support/docs/ip/generic-routing-encapsulation-gre/25885-pmtudipfrag.html (there is some
examples of how TCP MSS avoids IP Fragmentation in this link but it is too long so if you want to read please visit this
link) Note: IP fragmentation involves breaking a datagram into a number of pieces that can be reassembled later.
QUESTION 7
Which algorithms are used to secure REST API from brute attacks and minimize the impact?
A. SHA-512 and SHA-384
B. MD5 algorithm-128 and SHA-384
C. SHA-1, SHA-256, and SHA-512
D. PBKDF2, BCrypt, and SCrypt
Correct Answer: D
One of the best practices to secure REST APIs is using password hash. Passwords must always be hashed to protect
the system (or minimize the damage) even if it is compromised in some hacking attempts. There are many such
hashing
algorithms which can prove really effective for password security e.g. PBKDF2, bcrypt and scrypt algorithms.
Other ways to secure REST APIs are: Always use HTTPS, Never expose information on URLs (Usernames, passwords,
session tokens, and API keys should not appear in the URL), Adding Timestamp in Request, Using OAuth, Input
Parameter Validation.
Reference: https://restfulapi.net/security-essentials/
We should not use MD5 or any SHA (SHA-1, SHA-256, SHA-512…) algorithm to hash passwords as they are not totally
secure. Note: A brute-force attack is an attempt to discover a password by systematically trying every possible
combination of letters, numbers, and symbols until you discover the one correct combination that works.
QUESTION 8
What are two differences between the RIB and the FIB? (Choose two.)
A. The FIB is derived from the data plane, and the RIB is derived from the FIB.
B. The RIB is a database of routing prefixes, and the FIB is the Information used to choose the egress interface for each
packet.
C. FIB is a database of routing prefixes, and the RIB is the information used to choose the egress interface for each
packet.
D. The FIB is derived from the control plane, and the RIB is derived from the FIB.
E. The RIB is derived from the control plane, and the FIB is derived from the RIB.
Correct Answer: BE
The Forwarding Information Base (FIB) contains destination reachability information as well as next-hop information.
This information is then used by the router to make forwarding decisions. The FIB allows for very efficient and easy
lookups.
QUESTION 9
What is a fact about Cisco EAP-FAST?
A. It does not require a RADIUS server certificate.
B. It requires a client certificate.
C. It is an IETF standard.
D. It operates in transparent mode.
Correct Answer: A
QUESTION 10
How does Cisco Trustsec enable more access controls for dynamic networking environments and data centers?
A. uses flexible NetFlow
B. assigns a VLAN to the endpoint
C. classifies traffic based on the contextual identity of the endpoint rather than its IP address
D. classifies traffic based on advanced application recognition
Correct Answer: C
QUESTION 11
What does the LAP send when multiple WLCs respond to the CISCO_CAPWAPCONTROLLER.localdomain hostname
during the CAPWAP discovery and join process?
A. broadcast discover request
B. join request to all the WLCs
C. unicast discovery request to each WLC
D. Unicast discovery request to the first WLS that resolves the domain name
Correct Answer: D
QUESTION 12
“HTTP/1.1 204 No Content” is returned when the curl -i -X DELETE command is issued. Which situation has occurred?
A. The object could not be located at the URI path.
B. The command succeeded in deleting the object.
C. The object was located at the URI, but it could not be deleted.
D. The URI was invalid.
Correct Answer: B
QUESTION 13
What is a Type 1 hypervisor?
A. runs directly on a physical server and depends on a previously installed operating system
B. runs directly on a physical server and includes its own operating system
C. runs on a virtual server and depends on an already installed operating system
D. run on a virtual server and includes its own operating system
Correct Answer: B
Get the latest and complete Cisco CCNP 350-401 exam dumps! Help you pass the first exam successfully! Click here for more…
Cisco CCNP 350-401 Exam Certification Coupon Code 2021
You have read my entire article, and I have already told you how to successfully pass the Cisco CCNP 350-401 exam.
You can choose: https://www.leads4pass.com/350-401.html and go directly to 350-401 Exam dumps channel! Get your key to successfully pass the exam!
Wish you be happy!
ps.
Get free Cisco 350-401 dumps PDF online: https://drive.google.com/file/d/1aqRKfJ-HNAIYoPpKINhJZh-wSL0b07KL/