
We have updated 350-701 Dumps. Contains 392 new exam questions to help you pass the 350-701 SCOR Exam effectively.
The full name of the 350-701 exam is Implementing and Operating Cisco Security Core Technologies (SCOR). You need to know all the core technologies including:
Network security
Cloud security
Content security
Endpoint protection and detection
Secure network access
Visibility and enforcement
Rest assured that the 350-701 dumps include all core technical exam questions, and have practical exam room experience to ensure you pass the 350-701 SCOR Exam with ease.
leads4pass 350-701 Dumps Questions https://www.leads4pass.com/350-701.html: Contains two study modes, PDF and VCE, you can choose to help you study easily in any environment and finally get a high score of 350-701 SCOR Exam.
You can experience a 350-701 free dumps online
QUESTION 1
Which two features of Cisco DNA Center are used in a Software-Defined Network solution? (Choose two)
A. accounting
B. assurance
C. automation
D. authentication
E. encryption
Correct Answer: BC
QUESTION 2
A network engineer is configuring DMVPN and entered the crypto is amp key cisc0380739941 address 0.0.0.0
command on host A The tunnel is not being established to host B. What action is needed to authenticate the VPN?
A. Enter the same command on host B.
B. Enter the command with a different password on host B.
C. Change isakmp to ikev2 in the command on host A.
D. Change the password on host A to the default password.
Correct Answer: A
QUESTION 3
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
A. Time-based one-time passwords
B. Data loss prevention
C. Heuristic-based filtering
D. Geolocation-based filtering
E. NetFlow
Correct Answer: BD
QUESTION 4
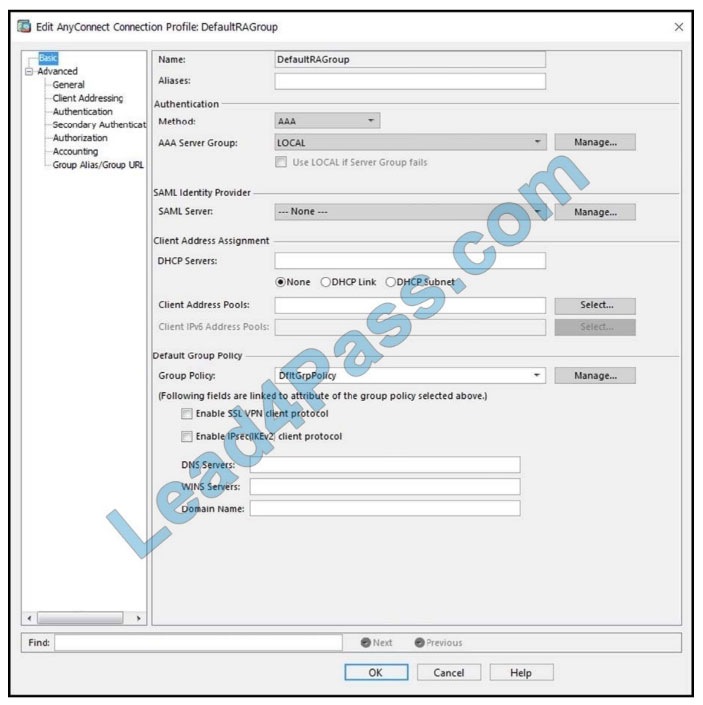
Refer to the exhibit. When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator
would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine
certificates. Which configuration item must be modified to allow this?
A. Group Policy
B. Method
C. SAML Server
D. DHCP Servers
Correct Answer: B
In order to use AAA along with an external token authentication mechanism, set the “Method” as “Both” in the
Authentication.
QUESTION 5
What are the two rootkit types? (Choose two)
A. registry
B. virtual
C. bootloader
D. user mode
E. buffer mode
Correct Answer: CD
The term rootkit\\' originally comes from the Unix world, where the wordroot\’ is used to describe a user with the highest possible level of access privileges, similar to an Administrator\\’ in Windows. The wordkit\’ refers to the software that grants root-level access to the machine. Put the two together and you get `rootkit\’, a program
that gives someone? with legitimate or malicious intentions? privileged access to a computer. There are four main types of rootkits: Kernel rootkits, User-mode rootkits, Bootloader rootkits, Memory rootkits
QUESTION 6
Which two descriptions of AES encryption are true? (Choose two)
A. AES is less secure than 3DES.
B. AES is more secure than 3DES.
C. AES can use a 168-bit key for encryption.
D. AES can use a 256-bit key for encryption.
E. AES encrypts and decrypts a key three times in sequence.
Correct Answer: BD
QUESTION 7
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all
users on that switch are unable to communicate with any destination. The network administrator checks the interface
status of all interfaces, and there is no err-disabled interface. What is causing this problem?
A. DHCP snooping has not been enabled on all VLANs.
B. The IP arp inspection limit command is applied on all interfaces and is blocking the traffic of all users.
C. Dynamic ARP Inspection has not been enabled on all VLANs
D. The no IP arp inspection trust command is applied on all user host interfaces
Correct Answer: D
Dynamic ARP inspection (DAI) is a security feature that validates ARP packets in a network. It intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from certain man-in-middle attacks. After enabling DAI, all ports become untrusted ports.
QUESTION 8
An engineer is configuring AMP for endpoints and wants to block certain files from executing. Which outbreak control method is used to accomplish this task?
A. device flow correlation
B. simple detections
C. application blocking list
D. advanced custom detections
Correct Answer: C
QUESTION 9
A Cisco ESA network administrator has been tasked to use a newly installed service to help create policy based on the
reputation verdict. During testing, it is discovered that the Cisco ESA is not dropping files that have an undetermined
verdict. What is causing this issue?
A. The policy was created to send a message to quarantine instead of drop
B. The file has a reputation score that is above the threshold
C. The file has a reputation score that is below the threshold
D. The policy was created to disable file analysis
Correct Answer: D
Maybe the “newly installed service” in this Qmentions about Advanced Malware Protection (AMP) can be used
along with ESA. AMP allows superior protection across the attack continuum.+ File Reputation? captures a fingerprint of each file as it traverses the ESA and sends it to AMP\’s cloud-based intelligence network for a reputation verdict. Given these results, you can automatically block malicious files and apply an administrator-defined policy.+ File Analysis? provides the ability to analyze unknown files that are traversing the ESA. A highly secure sandbox environment enables AMP to glean precise details about the file\’s behavior and to combine that data with detailed human and machine analysis to determine the file\’s threat level. This disposition is then fed into AMP cloud-based intelligence network and used to dynamically update and expand the AMP cloud data set for enhanced protection
QUESTION 10
A network engineer is deciding whether to use stateful or stateless failover when configuring two ASAs for high
availability. What is the connection status in both cases?
A. need to be reestablished with stateful failover and preserved with stateless failover
B. preserved with stateful failover and needs to be reestablished with stateless failover
C. preserved with both stateful and stateless failover
D. need to be reestablished with both stateful and stateless failover
Correct Answer: B
QUESTION 11
Which two preventive measures are used to control cross-site scripting? (Choose two)
A. Enable client-side scripts on a per-domain basis.
B. Incorporate contextual output encoding/escaping.
C. Disable cookie inspection in the HTML inspection engine.
D. Run untrusted HTML input through an HTML sanitization engine.
E. Same Site cookie attribute should not be used.
Correct Answer: AB
QUESTION 12
Which type of encryption uses a public key and a private key?
A. Asymmetric
B. Symmetric
C. Linear
D. Nonlinear
Correct Answer: A
QUESTION 13
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two)
A. DDoS
B. antispam
C. antivirus
D. encryption
E. DLP
Correct Answer: DE
……
350-701 Free Dumps Online Download:https://drive.google.com/file/d/15v-6KMDKCqNH7qcN7oDv9foO6H0qQ08p/view?usp=sharing
Use the updated 350-701 dumps https://www.leads4pass.com/350-701.html for complete 350-701 SCOR Exam resources to help you successfully pass the Implementing and Operating Cisco Security Core Technologies (SCOR) exam on your first attempt.