
Leads4pass 350-701 Dumps 2025 exam preparation materials are fully updated and contain 753 latest exam questions and answers, which are truly effective. The exam questions are based on the actual exam environment and include a variety of exam question types:
| Total Questions: | 753 |
| Single & Multiple Choice: | 727 |
| Drag Drop: | 26 |
Leads4Pass provides complete 350-701 SCOR exam preparation materials, download 350-701 dumps PDF or 350-701 dumps VCE: https://www.leads4pass.com/350-701.html, to help you easily plan your career path in 2025.
Next, you can continue to participate in the cisco 350-701 online practice test, and at the end of the article, we share issues that candidates are concerned about:
Online practice 2025 cisco 350-701 dumps exam questions
| Number of exam questions | Exam name | From | Release time | Related exams |
| 15 | Implementing and Operating Cisco Security Core Technologies (SCOR) | leads4pass | 2025 | CCNP Security |
Download 350-701 dumps exam questions and answers (You can read it anytime)
New Question 1:
Which two descriptions of AES encryption are true? (Choose two)
A. AES is less secure than 3DES.
B. AES is more secure than 3DES.
C. AES can use a 168-bit key for encryption.
D. AES can use a 256-bit key for encryption.
E. AES encrypts and decrypts a key three times in sequence.
Correct Answer: BD
https://gpdb.docs.pivotal.io/43190/admin_guide/topics/ipsec.html
New Question 2:
An organization wants to use Cisco FTD or Cisco ASA devices. Specific URLs must be blocked from being accessed via the firewall which requires that the administrator input the bad URL categories that the organization wants blocked into the access policy. Which solution should be used to meet this requirement?
A. Cisco ASA because it enables URL filtering and blocks malicious URLs by default, whereas Cisco FTD does not
B. Cisco ASA because it includes URL filtering in the access control policy capabilities, whereas Cisco FTD does not
C. Cisco FTD because it includes URL filtering in the access control policy capabilities, whereas Cisco ASA does not
D. Cisco FTD because it enables URL filtering and blocks malicious URLs by default, whereas Cisco ASA does not
Correct Answer: C
New Question 3:
A network administrator has configured TACACS on a network device using the key Cisc0467380030 tor authentication purposes. However, users are unable to authenticate. TACACS server is reachable, but authentication is tailing. Which configuration step must the administrator complete?
A. Implement synchronized system clock on TACACS server that matches the network device.
B. Install a compatible operating system version on the TACACS server.
C. Configure the TACACS key on the server to match with the network device.
D. Apply an access control list on TACACS server to allow communication with the network device.
Correct Answer: C
Explanation: For TACACS authentication to work, the key configured on the network device must match the key configured on the TACACS server. If users are unable to authenticate despite the TACACS server being reachable, it is likely due to a mismatch in the keys. Ensuring that both the network device and the TACACS server have the same key configured is crucial for successful authentication.
New Question 4:
A user has a device in the network that is receiving too many connection requests from multiple machines. Which type of attack is the device undergoing?
A. phishing
B. slowloris
C. pharming
D. SYN flood
Correct Answer: D
New Question 5:
An organization is using CSR1000v routers in their private cloud infrastructure. They must upgrade their code to address vulnerabilities within their running code version. Who is responsible for these upgrades?
A. The organization must update the code for the devices they manage.
B. The cloud vendor is responsible for updating all code hosted in the cloud.
C. The cloud service provider must be asked to perform the upgrade.
D. The CSR1000v is upgraded automatically as new code becomes available.
Correct Answer: A
New Question 6:
Which two behavioral patterns characterize a ping of death attack? (Choose two)
A. The attack is fragmented into groups of 16 octets before transmission.
B. The attack is fragmented into groups of 8 octets before transmission.
C. Short synchronized bursts of traffic are used to disrupt TCP connections.
D. Malformed packets are used to crash systems.
E. Publicly accessible DNS servers are typically used to execute the attack.
Correct Answer: BD
Ping of Death (PoD) is a type of Denial of Service (DoS) attack in which an attacker attempts to crash,destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.A correctly- formed ping packet is typically 56 bytes in size, or 64 bytes when the ICMP header is considered,and 84 including Internet Protocol version 4 header.
However, any IPv4 packet (including pings) may be as large as 65,535 bytes. Some computer systems were never designed to properly handle a ping packet larger than the maximum packet size because it violates the Internet Protocol documentedLike other large but well-formed packets, a ping of death is fragmented into groups of 8 octets beforetransmission.
However, when the target computer reassembles the malformed packet, a buffer overflow can occur, causing a system crash and potentially allowing the injection of malicious code.
New Question 7:
Which algorithm is an NGE hash function?
A. HMAC
B. SHA-1
C. MD5
D. SISHA-2
Correct Answer: D
New Question 8:
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
A. biometric factor
B. time factor
C. confidentiality factor
D. knowledge factor
E. encryption factor
Correct Answer: AD
Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor- authentication.html
The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint,face, and retina scans. Biometrics is used commonly in mobile devices).
New Question 9:
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this requirement using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor?
A. Configure a Cisco FMC to send syslogs to Cisco Stealthwatch Cloud
B. Deploy the Cisco Stealthwatch Cloud PNM sensor that sends data to Cisco Stealthwatch Cloud
C. Deploy a Cisco FTD sensor to send network events to Cisco Stealthwatch Cloud
D. Configure a Cisco FMC to send NetFlow to Cisco Stealthwatch Cloud
Correct Answer: B
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2019/pdf/5eU6DfQV/LTRSEC-2240-LG2.pdf
New Question 10:
Which license is required for Cisco Security Intelligence to work on the Cisco Next Generation Intrusion Prevention System?
A. control
B. malware
C. URL filtering
D. protect
Correct Answer: D
New Question 11:
Refer to the exhibit.
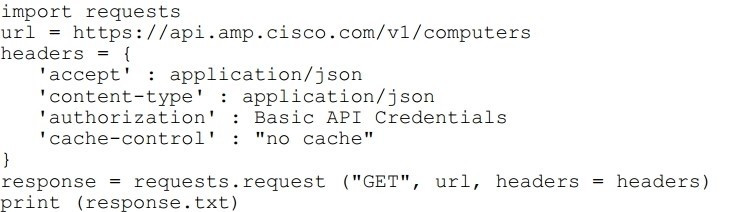
What will happen when this Python script is run?
A. The compromised computers and malware trajectories will be received from Cisco AMP
B. The list of computers and their current vulnerabilities will be received from Cisco AMP
C. The compromised computers and what compromised them will be received from Cisco AMP
D. The list of computers, policies, and connector statuses will be received from Cisco AMP
Correct Answer: D
New Question 12:
Which attack is preventable by Cisco ESA but not by the Cisco WSA?
A. buffer overflow
B. DoS
C. SQL injection
D. phishing
Correct Answer: D
New Question 13:
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center?
A. quality of service
B. time synchronization
C. network address translations
D. intrusion policy
Correct Answer: B
New Question 14:
Refer to the exhibit.
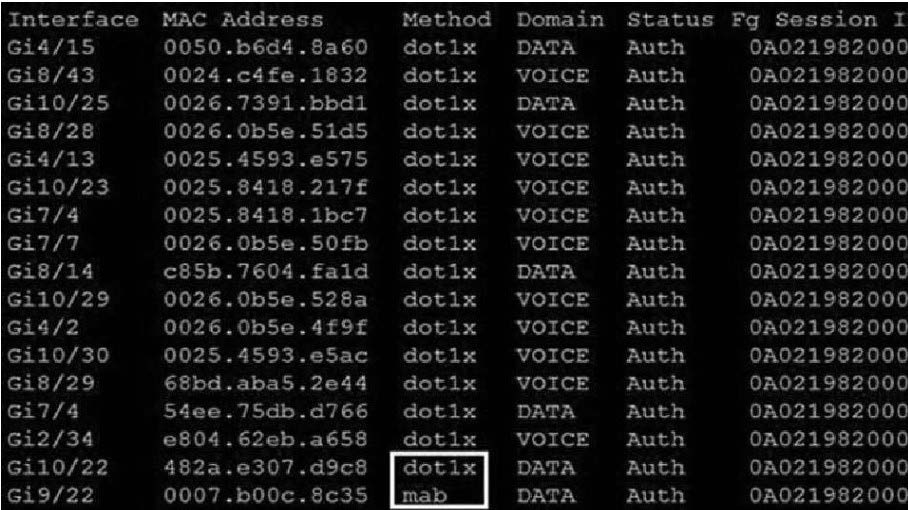
Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
A. show authentication registrations
B. show authentication method
C. show dot1x all
D. show authentication sessions
Correct Answer: D
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/s1/sec-s1-xe-3se- 3850-cr-book/sec-s1-xe-3se-3850-cr-book_chapter_01.html#wp3404908137 Displaying the Summary of All Auth Manager Sessions on the Switch Enter the following:
Switch# show authentication sessions Interface MAC Address Method Domain Status Session ID Gi1/48 0015.63b0.f676 dot1x DATA Authz Success 0A3462B1000000102983C05C Gi1/5 000f.23c4.a401 mab DATA Authz Success 0A3462B10000000D24F80B58 Gi1/5 0014.bf5d.d26d dot1x DATA Authz Success 0A3462B10000000E29811B94
New Question 15:
What are two workload security models? (Choose two.)
A. SaaS
B. PaaS
C. off-premises
D. on-premises
E. IaaS
Correct Answer: AD
Download 350-701 dumps exam questions and answers (You can read it anytime)
In summary:
The above are the latest free Cisco 350-701 dumps exam practice materials. You are welcome to download the latest and complete 350-701 dumps in 2025: https://www.leads4pass.com/350-701.html, 763 exam questions and answers , real and effective, and the best exam preparation material.
Cisco 350-701 FAQs
2025 Cisco 350-701 Exam Details
- 350-701 SCOR is a 120-minute exam that tests candidates’ knowledge of implementing and operating core security technologies, including network security, cloud security, content security, endpoint protection and detection, secure network access, visibility, and enforcement.
- Candidates can choose Japanese or English, depending on your geographical location and the language you are good at. The registration fee is 400$, or you can use cisco learning points. After that, you need to prepare for the exam according to the study plan, and the exam time is 120 minutes.
- It is recommended that you read 350-701 SCOR official information in full to understand real-time news, download the SCOR exam topics and read all contents carefully, and use exam preparation materials to solve all difficult questions.
Is cisco 350-701 SCOR certification worth it in 2025?
Cisco 350-701 SCOR certification is part of the CCNP security track, which has a high reputation in the field of network security. You know that since the arrival of AI, many careers have been impacted, but network security has become more and more important. You can imagine how it will be in the future. The gold content will be higher, so it will be very valuable in 2025.
Will the salary for cisco 350-701 SCOR certification increase in 2025?
Salary growth is determined by many factors: experience level, location, position, company strength, economic environment, etc.
For holders who have just obtained the 350-701 SCOR certification, their salary will increase. As they develop in all aspects, their future salary will make a qualitative leap. I would say this is a popular course. Certification, you have high earning potential when you hold it.