
Cisco 200-201 CBROPS exam questions and answers from leads4pass 200-201 dumps!
Can Cisco 200-201 dumps help me pass the exam?
Yes! Get the complete Cisco 200-201 dumps with PDF and VCE: https://www.leads4pass.com/200-201.html (187 Q&A dumps PDF+VCE) [2022.6 Updated] Total Questions: 245 Q&A
Are the free Cisco 200-201 exam questions and answers up-to-date?
Yes, the free Cisco 200-201 exam questions are part of the leads4pass 200-201 dumps. For 100% passing of the exam, please get the instant update Cisco 200-201 exam dumps at leads4pass.
What if I fail the Cisco 200-201 exam?
leads4pass has a pass rate of more than 99%. As long as you study the latest exam dump carefully, you are guaranteed to pass the exam easily. If you are not at ease, you can check the leads4pass policy page, which contains a detailed description of the processing method in case of failure. A full refund is guaranteed.
If you have more questions, please contact leads4pass customer service or email, leads4pass will reply to you within 24 hours. Please take the online exam next!
Reminder: The test questions we share for free each time are Q1-Q12, or more, and there will never be a continuous update of the question number because all the updated test questions are the latest version. We guarantee that each free shared test Question can improve your skills!
[2022.6 Updated] Free share Cisco 200-201 Exam Question
QUESTION 1:
Refer to the exhibit.
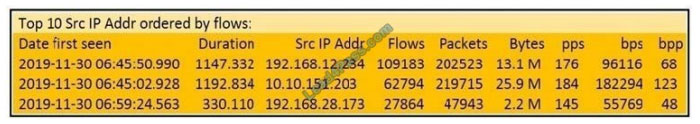
What information is depicted?
A. IIS data
B. NetFlow data
C. network discovery event
D. IPS event data
Correct Answer: B
QUESTION 2:
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
A. social engineering
B. eavesdropping
C. piggybacking
D. tailgating
Correct Answer: A
QUESTION 3:
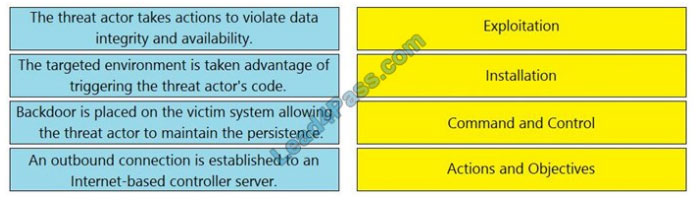
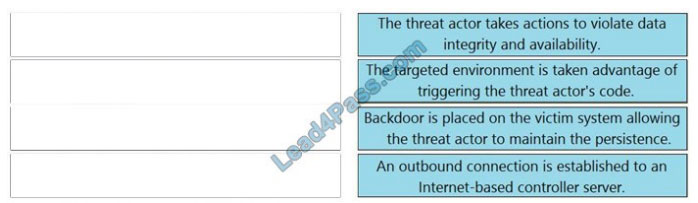
DRAG-DROP
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Select and Place:
Correct Answer:
QUESTION 4:
What is an example of social engineering attacks?
A. receiving an unexpected email from an unknown person with an attachment from someone in the same company
B. receiving an email from human resources requesting a visit to their secure website to update contact information
C. sending a verbal request to an administrator who knows how to change an account password
D. receiving an invitation to the department\’s weekly WebEx meeting
Correct Answer: C
QUESTION 5:
DRAG-DROP
Drag and drop the type of evidence from the left onto the description of that evidence on the right.
Select and Place:
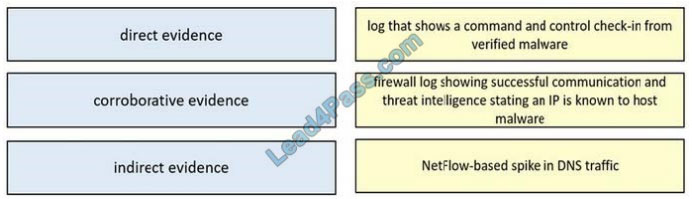
Correct Answer:
……
Get more up-to-date free Cisco 200-201 exam questions and answers: click here
Cisco 200-201 online exam test
Exam answers are announced at the end of the article
QUESTION 1
What are the two characteristics of the full packet captures? (Choose two.)
A. Identifying network loops and collision domains.
B. Troubleshooting the cause of security and performance issues.
C. Reassembling fragmented traffic from raw data.
D. Detecting common hardware faults and identify faulty assets.
E. Providing a historical record of a network transaction.
QUESTION 2
Which system monitors local system operation and local network access for violations of a security policy?
A. host-based intrusion detection
B. systems-based sandboxing
C. host-based firewall
D. antivirus
QUESTION 3
What is a benefit of agent-based protection when compared to agentless protection?
A. It lowers maintenance costs
B. It provides a centralized platform
C. It collects and detects all traffic locally
D. It manages numerous devices simultaneously
QUESTION 4
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist
group.
What is the initial event called in the NIST SP800-61?
A. online assault
B. precursor
C. trigger
D. instigator
QUESTION 5
One of the objectives of information security is to protect the CIA of information and systems.
What does CIA mean in this context?
A. confidentiality, identity, and authorization
B. confidentiality, integrity, and authorization
C. confidentiality, identity, and availability
D. confidentiality, integrity, and availability
QUESTION 6
Which signature impacts network traffic by causing legitimate traffic to be blocked?
A. false negative
B. true positive
C. true negative
D. false positive
QUESTION 7
Which action prevents buffer overflow attacks?
A. variable randomization
B. using web based applications
C. input sanitization
D. using a Linux operating system
QUESTION 8
Which event is user interaction?
A. gaining root access
B. executing remote code
C. reading and writing file permission
D. opening a malicious file
QUESTION 9
What is a difference between an inline and a tap mode traffic monitoring?
A. Tap mode monitors packets and their content with the highest speed, while the inline mode draws a packet path for
analysis.
B. Inline monitors traffic without examining other devices, while a tap mode tags traffic and examines the data from
monitoring devices.
C. Inline mode monitors traffic path, examining any traffic at a wire speed, while a tap mode monitors traffic as it crosses
the network.
D. Tap mode monitors traffic direction, while inline mode keeps packet data as it passes through the monitoring
devices.
QUESTION 10
What is the virtual address space for a Windows process?
A. physical location of an object in memory
B. set of pages that reside in the physical memory
C. system-level memory protection feature built into the operating system
D. set of virtual memory addresses that can be used
QUESTION 11
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its
integrity?
A. examination
B. investigation
C. collection
D. reporting
QUESTION 12
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions.
Which identifier tracks an active program?
A. application identification number
B. active process identification number
C. runtime identification number
D. process identification number
Publish the answer
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 |
| CE | C | B | B | D | D | C | D | C | D | C | D |
PS. And share part of the Cisco 200-201 exam PDF download for free: https://drive.google.com/file/d/1lG3DdqAT505ibWpn4WQX0j0yNasx1mwY/
Cisco 200-201 CBROPS exam is a newly updated exam item from 2020-2022. Any new Cisco item is an opportunity.
Choose leads4pass 200-201 dumps: https://www.leads4pass.com/200-201.html (187 Q&A dumps PDF+VCE) Help you pass the first exam successfully.